Surge in attacks exploiting old ThinkPHP and ownCloud flaws

Increased hacker activity has been observed in attempts to compromise poorly maintained devices that are vulnerable to older security issues from 2022 and 2023.
Threat monitoring platform GreyNoise is reporting spikes in actors leveraging CVE-2022-47945 and CVE-2023-49103 that affect ThinkPHP Framework and the open-source ownCloud solution for file sharing and syncing.
Both vulnerabilities have critical severity and can be exploited to execute arbitrary operating system commands or to obtain sensitive data (e.g. admin password, mail server credentials, license key).
The first vulnerability is a local file inclusion (LFI) issue in the language parameter of ThinkPHP Framework before 6.0.14. An unauthenticated remote attacker can leverage it to execute arbitrary operating system commands in deployments where the language pack feature is enabled.
Akamai reported last summer that Chinese threat actors have been leveraging the flaw since October 2023 in narrow-scope operations.
According to threat monitoring platform GreyNoise, CVE-2022-47945 is under high-volume exploitation right now, with attacks launched from a growing number of source IPs.
“GreyNoise has observed 572 unique IPs attempting to exploit this vulnerability, with activity increasing in recent days,” warns the bulletin.
This is despite its low Exploit Prediction Scoring System (EPSS) rating of 7% and the flaw not being included in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
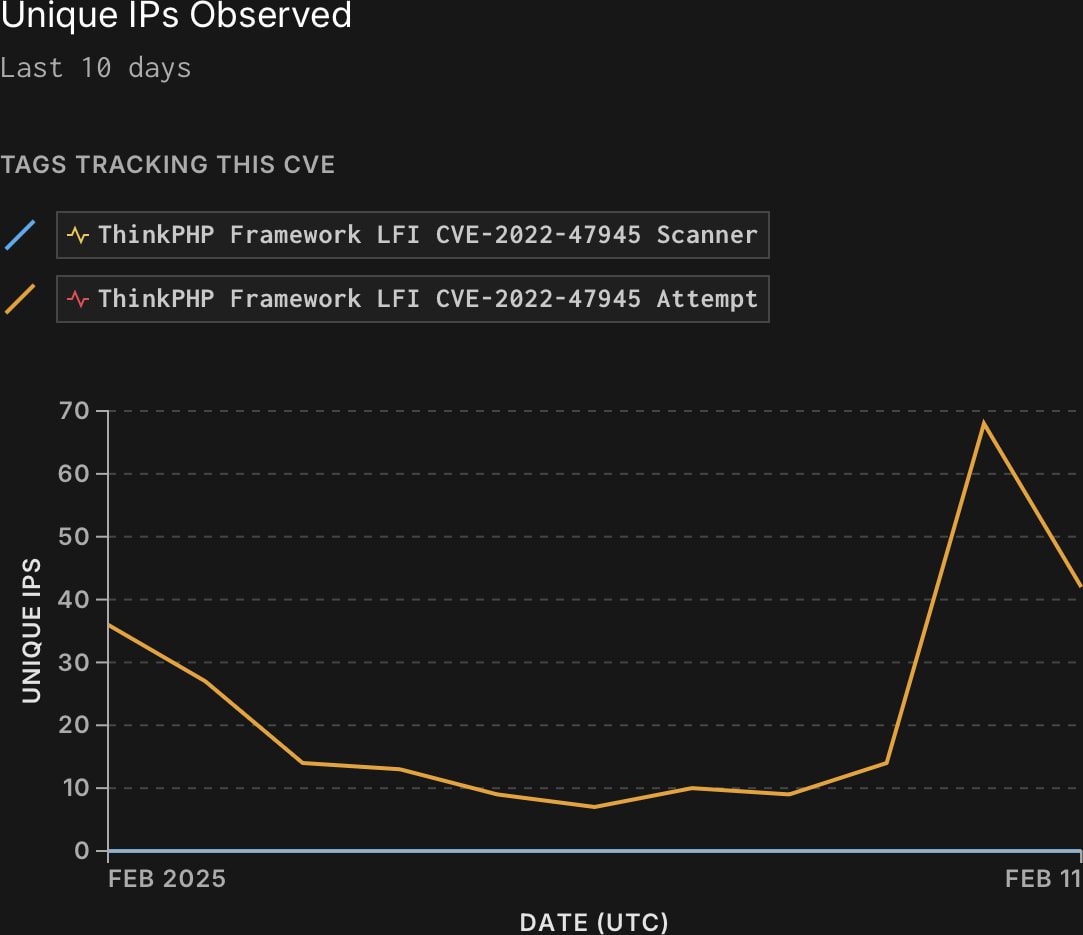
Source: Greynoise
The second vulnerability affects the popular open-source file-sharing software and arises from the app’s dependency on a third-party library that exposes PHP environment details through a URL.
Soon after the vulnerability’s initial disclosure from the developers in November 2023, hackers started exploiting it to steal sensitive information from unpatched systems.
A year later, CVE-2023-49103 was listed by the FBI, CISA, and NSA, among the 15 most exploited vulnerabilities of 2023.
Despite over 2 years having passed since the vendor released an update that addresses the security issue, many instances remain unpatched and exposed to attacks.
GreyNoise observed increased exploitation of CVE-2023-49103 recently, with malicious activity originating from 484 unique IPs.
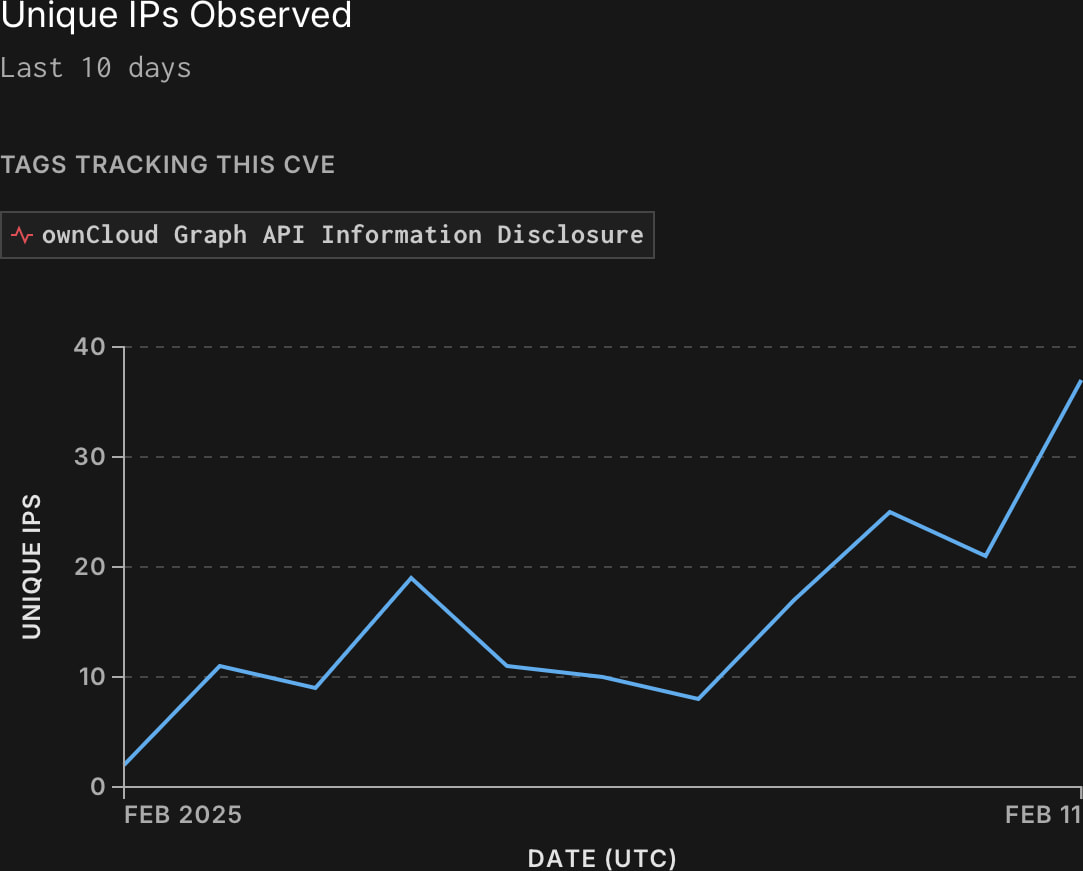
Source: Greynoise
To safeguard systems against active exploitation users are advised to upgrade to ThinkPHP 6.0.14 or later, and ownCloud GraphAPI to 0.3.1 and newer.
It is also recommended that potentially vulnerable instances are taken offline or placed behind a firewall to reduce the attack surface.
Source link








